Solution
Cybersecurity

Cybersecurity refers to the people, processes, and technologies used to protect computer systems, networks, and sensitive information from unauthorized access, theft, damage, or disruption. With the increasing dependence on digital technologies in today’s world, cybersecurity has become a critical concern for individuals, organizations, and governments.
Some of the common cybersecurity threats include malware, phishing attacks, social engineering, denial-of-service attacks, ransomware, and insider threats. These threats can cause significant damage to organizations, resulting in financial losses, reputational damage, and legal liabilities.
To mitigate the threats, cybersecurity involves multiple layers of protection, including:
- Network security
- Endpoint security
- Application security
- Data security
- Security Operation Center
These layers of protection work together to prevent cyber attacks and mitigate the impact of any successful attacks.


Network Security
Several component which organizations may need to protect their network:
- Firewalls
- Access Control
- SD-WAN
- Secure Access Service Edge (SASE)
- Network Antivirus and Anti-Malware Software
- Network Encryption
- Network Sandboxing
- Intrusion Detection and Prevention Systems (IDPS)
- DNS Security
- Virtual Private Networks (VPNs)

Endpoint Security
In today’s world, cyber threats are evolving and becoming more sophisticated, making it crucial for organizations to secure their end point devices. End point devices such as desktops, laptops, smartphones, tablets, point-of-sale (POS) systems, and Internet of Things (IoT) devices are frequently used by end users and connected to the internet. These devices provide access to sensitive data and critical systems, making them a prime target for cyber attackers.
With the increasing number of end point devices used in organizations, the threat landscape is constantly expanding, and it is essential to take proactive measures to protect against various security threats such as viruses, malware, data leaks, and ransomware attacks.
There are several solutions which you may need to secure end point devices such as:
- Unified Endpoint Manager
- Endpoint Antivirus
- Data Loss Prevention
- Disk Encryption
Application Security
Several solutions which can help to secure your environment in the application level:
- Web Application Firewall (WAF)
- Anti-bot Security
- Application Performance Manager (APM)
- Security Information and Event Management (SIEM)
- Security Orchestration and Automated Response (SOAR)
- User Behavior Analytics (UBA)
- Pentest Tools


Data Security
Here are some general steps you can take to build data security:
- Identify and classify sensitive data
- Use encryption
- Use strong authentication
- Implement access controls
- Secure your infrastructure
- Use security software
- Monitor for threats
- Develop and test incident response plans
- Backup Software
- Cyber Recovery Solution
Backup Software
There are several benefits of using backup as a method of data security, including:

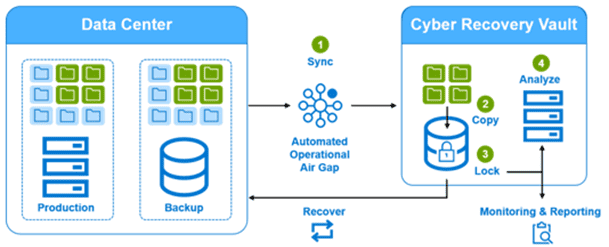
Cyber Recovery Solution
Some of the key features of Dell Cyber Recovery Solution include:
Security Operation Center
A Security Operations Center (SOC) is a centralized facility that provides an organization with the capability to detect, analyze, and respond to security threats and incidents. It is typically staffed with security analysts, incident responders, and other security professionals who monitor and manage the organization’s security infrastructure, systems, and applications.
The main goal of a SOC is to provide continuous monitoring and rapid response to security incidents, thereby minimizing the impact of an attack or breach. SOC teams use a range of tools, technologies, and processes to detect and respond to security incidents, such as intrusion detection and prevention systems, security information and event management (SIEM) tools, and incident response playbooks.
Some of the key functions of a SOC include:
The SOC delivers the following services:
- Proactive Monitoring of all the Cybersecurity Tools (24x7)
- Threat Hunting
- Incident Response and Recovery
- Remediation Activities
- Compliance
- Reporting on threats/vulnerabilities to other internal teams
- Providing recommendations to harden security posture
