The Cyber Recovery solution maintains mission-critical business data and technology configurations in a secure, air-gapped ‘vault’ environment that can be used for recovery or analysis. The Cyber Recovery Vault (CR Vault) is physically isolated from an unsecure system or network.
The Cyber Recovery solution enables access to the CR Vault only long enough to replicate data from the production system. At all other times, the CR Vault is secured and off the network. A deduplication process is performed in the production environment to expedite the replication process so that connection time to the CR Vault is as short as possible.
Within the CR Vault, the Cyber Recovery software creates point-in-time (PIT) retention-locked copies that can be validated and then used for recovery of the production system.
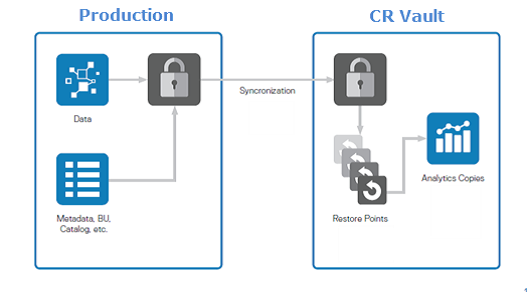
Pict 1. High Level Solution Architecture
Cyber Recovery architecture
As shown in the following diagram, the Cyber Recovery solution uses Data Domain systems to replicate data from the production system to the CR Vault through a dedicated replication data link.
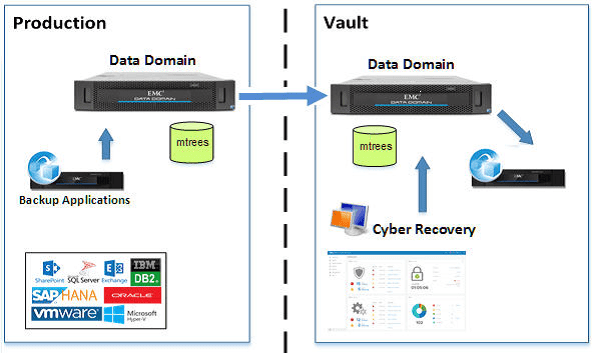
Pict 2. Cyber Recovery Archiceture
How the Dell EMC Cyber Recovery Vault Works To Help You Recover From Attacks?
Dell EMC Cyber Recovery is a complete, isolated recovery solution that can help you minimize downtime, expense, and lost revenue by providing a resilient backup to critical data and a path to recovery from a cyber attack. To start, Dell EMC offers professional services that help you assess, plan, implement, and validate your cyber recovery solution.
Production environments are vulnerable to attack. Dell EMC Cyber Recovery keeps your data in a vault, where it is physically and logically isolated from other systems and locations. Physically, the Cyber Recovery Vault resides in a restricted room or area in your facility accessible only by authorized physical access, which limits the ability of in-house saboteurs that wish to hold your data for ransom to complete their objectives.

Pict 3. Dell EMC Cyber Recovery
CyberSense security analytics looks for indicators of compromised data and can help you discover the who, how, and the why, so you can recover quickly from attack.
Source:
https://www.delltechnologies.com/en-id/data-protection/cyber-recovery-solution.htm

